Independent group’s trigger-happy copying : allegations that Irish newspapers have copied content from blogs. There’s been a lot of cases of this recently. good round-up from Cian Ginty
(tags: plagiarism ireland newspapers independent)
Month: August 2008
Review of bicycle helmet effectiveness studies : quite a few case-control studies consistently demonstrating the protective effects of bicycle helmet use on shared roadways
(tags: cycling helmets safety health statistics)Spammer-X’s numbers on spam profitability : he claimed that he made net $336k per year from spamming in 2004
(tags: via:tzink spammer-x spam money pay profit motives)
GoDaddy is rejecting mail with URLs that appear in the Spamhaus PBL. As this thread on the Amazon EC2 forum notes, this is creating false positives, causing nonspam mail to be rejected. Here’s what GoDaddy reportedly said about this policy:
Unfortunately, our system is set to reject mails sent from or including links listed in the SBL, PBL or XBL. Because the IP address associated to [REMOVED] is listed in the PBL, any emails containing a link to this site will be rejected. This includes plain-text emails including this information.
If this is true, it’s utterly broken.
Spamhaus explicitly warn that this is not to be done, on the PBL page:
Do not use PBL in filters that do any ‘deep parsing’ of Received headers, or for other than checking IP addresses that hand off to your mailservers.
And more explicitly in the Spamhaus PBL FAQ:
PBL should not be used for URI-based blocking! Consider the false positive potential: legitimate webservers hosted with services such as dyndns.com or ath.cx! Or consider that ISPs and other networks are encouraged to list any IP ranges which should not send mail, and that could include web servers! Use SBL or XBL (or sbl-xbl.spamhaus.org) for URI blocking as described in our Effective Spam Filtering section. Use PBL only for SMTP (mail).
Critically, the PBL now lists all Amazon EC2 space, since Spamhaus interpret Amazon’s policy as forbidding email to be delivered via direct SMTP from there. (Note — email, not HTTP.)
With this filter in place at GoDaddy, that now means that if you mail a URL of any page on any site hosted at EC2 to a user of GoDaddy, your mail won’t get through.
Note: this is much worse than blocks of SMTP traffic from EC2. In that case, an EC2 user can relay their legit SMTP traffic via an off-EC2 host. In this case, there is no similar option in HTTP that isn’t insufferably kludgy. :(
Dublin’s new M50 electronic toll tags : what a mess! there are no less than 8 tag operators and a bewildering array of prices and penalties. typical
(tags: ireland dublin m50 tolls roads pricing)Sustained IO on EBS == No Bueno : worrying stats for Amazon EBS data throughput, dropping from 160 MB/s to a rather paltry 42.4 MB/s
(tags: amazon ebs ec2 speed networking hosting benchmarks)MXLogic on the economics of spam : Sam Masiello of MXLogic works out that phishers may be netting a 7300% profit margin; this is why spam’s not going away. mind you he does this by believing Gartner figures, which is never a good idea
(tags: sam-masiello mxlogic via:tzink phishing spam money)
Cian Ginty at the Irish Times writes:
As clunky helmets, yellow reflective gear, and Lycra could be used as a stereotype for Irish cyclists, it might come as a surprise that women wearing high heels are a common sight on bicycles in Copenhagen.
The general image of cycling here is vastly different to so-called bicycle cultures where cycling is normalised and there is talk of a “slow bicycle movement”.
“Among thousands and thousands of cyclists on my daily routes, I think I see one or two reflective vests a week, if that,” says Mikael Colville-Andersen, a cycling advocate living in Copenhagen.
With Denmark, the Netherlands and Germany – where bicycle usage is high – the helmets and reflective clothing we think of as “a must” for cyclists are far from standard.
It then goes on to rehash some of the stuff that has cropped up recently on cycling blogs about cycling safety, helmets, etc.
The only problem with casualization of cycling, removing gear like helmets, is that without corresponding changes to the road and cycleways to make them safer, it will increase accidents and fatalities. I looked this up a couple of weeks back when I came across an anti-helmet site. Chasing up the figures and doing some research, it became clear that if you simply want to cycle without hurting yourself, the facts were not on their side — helmets save lives, especially when dealing with shared roadways as we have here.
Copenhagenization is a result of a better, safer road environment for cyclists, as seen in Denmark and the Netherlands, which makes safety gear not as much of a requirement. But on the other hand, Ireland’s roads are designed mainly for cars, and Dublin Council have done little to help — that makes safety gear a requirement, unfortunately :(
However, I think this is the real reason why people don’t cycle in Dublin:
Let’s take a fictional person, let’s call her Kassandra. Kassandra lives a little north of Copenhagen and rides every to work every day between 07:25 and 07:55 and back again between 15:35 and 16:05. Kassandra doesn’t mind a little light showers, but if the intensity increases to over 0.4 mm over 30 minutes (light rain), then she thinks it is too wet. Kassandra works five days a week and has weekends and holidays free. That gives her 498 trips between September 2002 and the end of August 2003.
How often does Kassandra get wet either to or from her job that year? The answer is, in fact, rarely. On those 498 trips it was only 17 times. That is only 3.5% or on average 1.5 trips a month.
3.5%. Compare that with what’s happened in Dublin this month — I’d estimate that’s meant that at least half of my rides have involved some degree of rainfall, occasioning many cries of woe.
It takes dedication — and lots of wet-weather gear — to ride a bike here…
(Of course, having said that, I look out the window and it’s immediately sunny ;)
Update: Ryan Meade corrects me in the comments:
Justin, you need to take a look at Owen Keegan’s paper to Velo-City 2005, “Weather and Cycling in Dublin : Perceptions and Reality”. The probability of getting wet is actually pretty comparable to the Copenhagen scenario detailed above – 5.5% for a 30 minute journey if you take 0.2mm per hour at the threshold for “getting wet”. On the other hand the vast majority of both cyclists and motorists think it’s more than 15%, with half thinking it’s above 30%.
Amazing how the psychological, “glass half-empty” factor influences my thinking on this. I had no idea!

I was away on holidays last week, and when I got back, I found my feed reader full of some good discussion as to whether today’s bigger spam botnets — Srizbi, Rustock, Mega-D, Cutwail/Pushdo — are sharing components, such as “landing” sites, exploits, customers, and even command and control networks. It started with this post on the FireEye Malware Intelligence Lab’s blog noting:
‘Some malware researchers have described Srizbi and Rustock as rival botnets, our data indicates that this apparent rivalry is a sibling rivalry at best. Srizbi and Rustock seem to be supported (controlled) by the same parent (bot herder).’
and in this followup:
‘We can clearly see that Srizbi, Pushdo and Rustock are using same ISP, and in many cases, IPs on the same subnet to host their Command and Control servers. It seems extremely unlikely to our research team that three previously “rival” Botnets would share nearly consecutive IP space, and be hosted in the same physical facility. Of all the data centers and IPs in the world, the fact that they are all on the same subnet is very intriguing. This fact makes the FireEye research team conclude that either the Botnets are operated by the same organization, or that the datacenter (McColo) is a shell corporation that leases out it’s IP space and bandwidth for nefarious actions.’ […]
‘IPs at a typical datacenter are leased out in a /30 or more commonly, a /29 block. However, here we can see that in a given succession of IPs, the three Botnets have C&C servers dispersed throughout. This gives us an impression that same Bot herder leased out a larger range and then distributed it amongst its different Botnets.’
Marshal say: ‘at the very least, the major botnets have common customers.’
Dark Reading cover it like so:
Rustock, which recently edged Srizbi for the top slot as the biggest spammer mostly due to a wave of fake Olympics and CNN news spam, and Srizbi, known for fake video and DVD spam, have been using the same Trojan, Trojan.Exchanger, to download their bot malware updates, researchers say. “This is the first time” we had seen this connection between the two botnets, says Fengmin Gong, chief security content officer for anti-botnet software firm FireEye. “That’s why when we saw it, it was surprising. They definitely have a relationship,” he says. “There’s not the rivalry we used to think about.” […]
Joe Stewart, director of security research for SecureWorks, says the Srizbi-Rustock connection is most likely due to a spammer using both zombie networks — not that the operators of the two botnets are actually collaborating. “What is confusing people is that you’re seeing Rustock bots sending out emails that essentially infect people with Srizbi, so they think it must be Srizbi that’s sending it, but it’s not,” he says. “Srizbi is not just one big model. It’s rented out to lots of different spammers.”
A major spammer may be trying to diversify by using the two botnets, he says. “It could be because they want to separate their malware-seeding operation from their spamming operation,” Stewart says. “Maybe their bots are getting blacklisted faster when they’re sending out URLs with fake video files because they’re easy to spot, so their spam doesn’t get through. So they send malware from this botnet, and spam from this one, to keep out of the blacklists longer.”
I agree that Joe’s scenario is very likely; the spammers aren’t always the same people who operate the botnets, and it only makes sense that some of them would spread their business among multiple nets, to minimize the risk that all of their output would be blocked if one ‘net runs into trouble (or indeed, good filtering ;). But seeing C&C servers sharing LANs also strikes me as unusual. One to watch.
Anyway, it’s good to see that the malware research blogs are now actively tracking and posting updates when the botnets change topics and format; this info is very valuable for us in anti-spam, as it allows us to map from the received spam mails back to the sending botnet, and determine which rules are good at detecting each botnet. Thanks, guys.
(image credit: cobalt123, used under CC license)
30% Of Internet Users Admit To Buying From Spam : ugh. we need a reminder of the Boulder Pledge. Mind you, Marshal have put out what appear to be inaccurate figures in the past regarding the Rustock botnet, so apply a pinch of salt
(tags: marshal spam boulder-pledge commerce shopping statistics via:techdirt)more details on EC2 Elastic Block Store : achieves 70MB/s on an m1.small instance; ‘performance exceeds what we’ve seen for filesystems striped across the four local drives of x-large instances’. pretty good for a network filesystem, although not great compared to fast local SATA disks. also: snapshots are incremental and perform nicely compared to local S3 copy-and-upload
(tags: ebs amazon performance benchmarks s3 ec2 disks snapshotting filesystems)Amazon Elastic Block Store (EBS) : ‘Prior to Amazon EBS, block storage within an Amazon EC2 instance was tied to the instance itself so that when the instance was terminated, the data within the instance was lost. Now with Amazon EBS, users can chose to allocate storage volumes that persist reliably and independently from Amazon EC2 instances.’ — can even snapshot to S3
(tags: amazon ebs ec2 aws s3 cloud-computing hosting)
Here’s my results for The Omnivore’s Hundred, a silly foodie “purity test”. Bold are items I’ve eaten; crossed-out items are ones I wouldn’t eat again. I score 70 out of 100, and clearly need to eat less Asian and more European cuisine ;)
- Venison
- Nettle tea
- Huevos rancheros
- Steak tartare
- Crocodile
- Black pudding
- Cheese fondue
- Carp
- Borscht
- Baba ghanoush
- Calamari
- Pho
- PB&J sandwich
- Aloo gobi
- Hot dog from a street cart
- Epoisses
- Black truffle
- Fruit wine made from something other than grapes
- Steamed pork buns
- Pistachio ice cream
- Heirloom tomatoes
- Fresh wild berries
- Foie gras
- Rice and beans
- Brawn, or head cheese
- Raw Scotch Bonnet pepper
- Dulce de leche
- Oysters
- Baklava
- Bagna cauda
- Wasabi peas
- Clam chowder in a sourdough bowl
- Salted lassi
- Sauerkraut
- Root beer float
- Cognac with a fat cigar
- Clotted cream tea
- Vodka jelly
- Gumbo
- Oxtail
- Curried goat
- Whole insects
- Phaal
- Goat’s milk
- Malt whisky from a bottle worth $120 or more
- Fugu
- Chicken tikka masala
- Eel
- Krispy Kreme original glazed doughnut
- Sea urchin
- Prickly pear
- Umeboshi
- Abalone
- Paneer
- McDonald’s Big Mac Meal
- Spaetzle
- Dirty gin martini
- Beer above 8% ABV
- Poutine
- Carob chips
- S’mores
- Sweetbreads
- Kaolin
- Currywurst
Durian- Frog’s Legs
- Beignets, churros, elephant ears or funnel cake
- Haggis
- Fried plantain
- Chitterlings or andouillette
- Gazpacho
- Caviar and blini
- Louche absinthe
- Gjetost or brunost
- Roadkill
- Baijiu
- Hostess Fruit Pie
- Snail
- Lapsang souchong
- Bellini
- Tom yum
- Eggs Benedict
- Pocky
- Tasting menu at a three-Michelin-star restaurant
- Kobe beef
- Hare
- Goulash
- Flowers
- Horse
- Criollo chocolate
- Spam
- Soft shell crab
- Rose harissa
- Catfish
- Mole poblano
- Bagel and lox
- Lobster Thermidor
- Polenta
- Jamaican Blue Mountain coffee
- Snake
(thanks to this generator and mordaxus at Emergent Chaos for the link.)
White Noise – An Electric Storm : 1969 album by David Vorhaus and Delia Derbyshire of the BBC Radiophonics Workshop: ‘one of the freakiest, most frightening, far out and forward thinking albums you may ever get to hear’
(tags: 1969 sixties music psych white-noise delia-derbyshire bbc radiophonics-workshop electronic)vim-flymake.vim : hooray! Flymake, on-the-fly compilation & error checking, for VIM. bit kludgy though, would be better if it integrated with vim 7.1’s “compiler” support
(tags: vim flymake compilers error-checking editors vi software)
non-PC devices increasing browser share : .5 – 1.5% of visitors to Warner music sites are now coming from games consoles and smartphones. bad news for Flash sites (via Torrez)
(tags: flash web browsers via:torrez warner-music os)full(4): always full device : ‘Writes to the /dev/full device will fail with an ENOSPC error. This can be used to test how a program handles disk-full errors.’ – that’s nifty. I can’t believe I’m still finding useful new UNIX features after 18 years
(tags: devices unix linux testing disks errors edge-cases enospc manual-pages)
2 Stage Transfer Drawing (advancing to a future state) on Vimeo : some great performance art from Irish artist Joan Healy; the installation appears to be a kiosk with a screen, and a touch pad. The pad itself is supposed to have a warm, soft, fleshy feel that ‘adds to the bond between people and machines’. However — in reality, it’s the artist’s back; she’s inside the kiosk, Mechanical Turk-style. Super-creepy
(tags: art creepy cool ireland joan-healy performance-art touchpads ui interface hci video)The Daily Show’s TiVo setup : cool details on how TDS captures the news networks’ TV output every day; they use TiVos, not MythTV. what they have works well enough, and that’s good enough for them (via Waxy)
(tags: mythtv tv the-daily-show tivo via:lhl)
Wow, this is pretty massive. The Irish Payment Services Organisation has again released details of a credit-card breach, this time on retail Point-of-Sale card terminals. Quoting the Irish Examiner story:
Una Dillon, head of card services at the Irish Payment Services Organisation, said the criminals went into the shops pretending to be doing maintenance work on behalf of the banks.
“We have discovered only in the last 48 hours that a number of retailers have been affected by a point-of-sale compromise,” she said. “We are in the lucky position that it was discovered quickly and the gardaí are working on it.
“Gardaí have uncovered a lot of the devices and CCTV footage. We have a list of all the card numbers that have been used. They have either been blocked or restrictions put on those cards.
“With the devices recovered it may just be that the cards were only saved and the criminals did not have a chance to get hold of the card numbers.”
“There will be an emergency meeting today with the gardaí, the terminal vendors and the banks to try and close down on this,” she said, adding the gardaí were in pursuit of the gang.
Insufficient authentication of maintainance staff is being blamed:
“The criminals have been going into shops claiming to be engineers working on the terminals. Staff are used to their bank officials coming to update terminals so unfortunately they have been able to do that.
Bank of Ireland estimated 3,100 of its debit and credit cards were affected and Ms Dillon said the other eight card providers could have similar numbers.
Bank of Ireland said, as a temporary measure, it had reduced the daily withdrawal limit on all its debit cards for ATM transactions outside Ireland to just €100 to protect customers from fraud.
They haven’t released the names of the affected shops yet; 20,000 cards, though, sounds like it’s been going on for while, on a large scale. Yikes.
The SiliconRepublic story claims that the gang ‘plugged in wireless devices that pushed the data to the internet and allowed the card numbers to be used overseas.’ However, in the past, these ‘wireless devices’ didn’t use the internet; instead they use parts from mobile phones, which relayed PINs, card numbers and CVV security codes via SMS text messages to Romania. That model seems more likely here, I would guess, due to the reliability of phone networks.
Update: last night’s RTE Six-One news bulletin (viewable as streaming RealVideo or transcoded 5MB AVI file), made it clear that the hardware used phone components and SMS. It had some pretty good pics of what appears to be a sample subverted POS terminal:



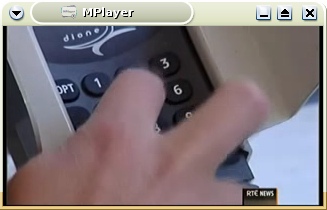


VISA have been warning about attacks on petrol-pump-based POS terminals since 2006, e.g. this story, but they’re more easy to attack since there’s few or no staff present by the pumps when the POS terminal subversion takes place. This has resulted in most petrol stations in Ireland disabling POS credit-card payment systems, requiring customers to pay at the counter; we lose convenience, but at least we’re probably not being skimmed. But these in-store POS terminals seem to be increasingly under attack; there are reports from Livigno, Italy, Rhode Island, and Canada.
The tamper-proofing of POS terminal hardware is unreliable; it’d be nice to see them made harder to tamper with. I would guess the gang used secondhand, hacked POS terminals, which supposedly should be tamper-evident (ie. easy to spot modifications).
Better yet, if Chip-and-PIN cards used end-to-end crypto between a crypto smartcard and the bank’s central systems, POS hacks would be impossible. But there’s no sign of that happening.
Most importantly, IPSO has promised that ‘banks will refund any customers whose details have been used to make fraudulent transactions.’ That’s key. It’s interesting to note that IPSO have been hammering home this point repeatedly in their stories — they’re worried about customer confidence, I’d guess.
The Evolution of Pre-Launch Gmail In Screenshots : fascinating! They really did a good job improving the UI, early revs were quite uninspiring
(tags: gmail google history email web ui)SealSkinz : waterproof socks and gloves — come recommended by Dublin’s cycle-couriers to avoid wet feet in all this bloody rain. lots and lots of good testimonials
(tags: dryness feet comfort clothing rain weather cycling outdoors socks gloves)
Emergent Chaos: Certifiably Silly : Adam Shostack tells the truth re Firefox 3’s stupid self-signed cert bug. ‘imposing yet another security tax, based on a static analysis of attackers and some certificate authority pixie dust, isn’t going to help things for very long.’
(tags: firefox firefox-3 security certificates ssl tls ca pki adam-shostack ui usability)Image Cerberus: a SpamAssassin plug-in against image spam : a new plugin, subject of a paper at this year’s CEAS conference it looks like
(tags: plugins spamassassin anti-spam image-spam images ceas conferences)Twitter drops SMS-notification support for EU users : interesting, I haven’t received the mail, and it claims to still be sending updates to my Irish mobile (update: I’m not actually *getting* any updates, though)
(tags: twitter phones mobile sms ireland eu uk)
A friend writes:
‘I switched my Vodafone bill to “online”, to cut down on junk mail. When I tried to log in to view my bill, I was asked for a second level password, specifically:
“your password is the last 4 digits of your customer number (which appears at the top of your phone bill). “
So, I can’t see my phone bill because I can’t see my phone bill.’

The Trifecta of FAIL : ah, the hazards of monkey-patching core classes illustrated perfectly; a Ruby point-release upgrade broke Rails (via chromatic)
(tags: ruby rails monkeypatching ouch programming coding oo subclassing apis)best intranet form ever : ‘The software my employer uses for booking holidays has recently been “upgraded” and we now need to specify an absence reason.’ there are several hundred reasons, including ‘Abortion’, ‘Stroke’, ‘Warts’, ‘Dementia’, ‘Rectal Problems’, ‘Manic Depression’ and, um, ‘Wax’. best of all, this is for booking time off in advance…
(tags: intranet funny inept hr wtf daily-wtf bureaucracy pto holidays)Sup : ‘a console-based email client for people with a lot of email [..] The goal of Sup is to become the email client of choice for nerds everywhere.’ Looks like they’ve nicked a few ideas from GMail, too (via Luis)
(tags: via:tieguy console linux unix sup mail mail-readers ui apps)
Cycle Helmets and Other Religious Symbols : there appears to be a lack of published research suggesting that bike helmets help avoid serious injury and death — in fact, research seems to suggest the _opposite_.
(tags: cycling helmets safety research bikes equipment)Clever method of near duplicate detection : ‘SIGIR 2008 paper, “SpotSigs: Robust and Efficient Near Duplicate Detection in Large Web Collections”‘. may be useful, although we’ve pretty much stopped deduping in SpamAssassin nowadays
(tags: corpora dupes duplicates spotsigs collections sigir papers via:jzawodny)HadoopStreaming : ‘Using the streaming system you can develop working hadoop jobs with extremely limited knowldge of Java. [..] Hadoop basically becomes a system for making pipes from shell-scripting work (with some fudging) on a cluster.’
(tags: hadoop perl streams unix distcomp clusters mapreduce)political zealot using GMail’s “this is spam” button to deliberately cause spamfilter problems for Obama’s campaign : ‘Tablemate at benihana confided how he subscribes to Obama’s mailing list and marks it all as spam to train Gmail. Urge to kill rising.’ – Kevin Fox on Twitter
(tags: twitter kevin-fox foaf-story benihana obama anti-spam filtering this-is-spam us-politics moveon)“Jake Leg” : ‘large numbers of [adulterated Prohibition-era alcohol, Jamaican Ginger Extract] users began to lose use of their hands and feet. Some victims could walk, but they had no control over the muscles which would normally have enabled them to point their toes upward. Therefore, they would raise their feet high with the toes flopping downward, which would touch the pavement first followed by their heels. The toe first, heel second pattern made a distinctive “tap-click, tap-click” sound as they walked. This very peculiar gait became known as the jake walk and those afflicted were said to have jake leg’
(tags: jake-leg walking history prohibition alcohol odd bizarre adulteration poison 1930s)
Luis Villa, in a post to FoRK:
I have found that [mail] threading is overrated, in part because I’ve realized that any conversation so baroque as to actually require threading probably isn’t worth following.
Even though I wrote a threader for MH, I have to admit by now that he has a point ;)
An Illustrated Guide to the Kaminsky DNS Vulnerability : great guide to Dan’s most recent discovery. it really is quite nasty (via Jeremy)
(tags: via:jzawodny dan-kaminsky dns security exploits bind)
Noted on Twitter:
simonw: So apparently http://www.news.com.au/ used json-time for their Beijing countdown widget and blew my App Engine quota! They’ve stopped now.
uh, great. That’s useful.
Google — how are we supposed to host useful services with those limits?
Green Karma – Carbon-offset your colo box must-read post from Chris. If you run a colo box, you should think about offsetting the ~2 tonnes of CO2 output it generates per year
sorenragsdale: Building a Cheap ZFS Server good set of details on MrN’s new ZFS-based home disk server
Malwebolence – The World of Web Trolling holy crap, those /b/tards are fucked up
TechCrunch UK campaigning for a “Digital Hub” I have to say, the Digital Hub is actually a great place to work; it’s well worth duplicating, if such a thing is possible
419eater anti-scammers fool 419ers into performing the Dead Parrot sketch “Possibly, he is pining for the fee-ords”
Google taking action against Nigerian/419 fraud spammers Good news. About time, too ;)